What is Multi-Factor/Two Factor Authentication?
When websites store your personal information, it’s important for your information to be protected. Many websites have user accounts that you can log into, using your password to verify (or authenticate) your identity. However, a password is not always enough to keep your personal information safe, so many websites utilise multi-factor authentication.
Multi-factor authentication is a mechanism that allows a user to access their account on a website or program after presenting two or more pieces of data to verify their identity. These pieces of data are called factors, and authentication requiring two factors (Two Factor Authentication) is most common today.
Authentication factors include:
- Something the user has - fob, keycard, QR code, or security token displayed on a device.
- Something the user knows - passwords, PIN, security question
- Something the user is - fingerprint, face, voice or iris recognition
- Somewhere the user is - access to a website may require only a PIN when the user is in the “approved” location/network, but require a PIN and a security token when outside the approved location.
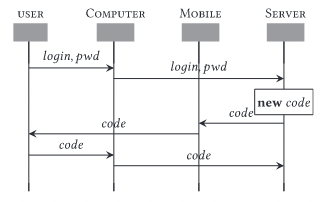
The most well-known method of Two-Factor Authentication is requiring both a password (something the user knows), and a single-use passkey (something the user has).
Often, this is implemented by the user providing their phone number to the website as part of their sign-up, and, during subsequent sign-in attempts, the website automatically sends a SMS (text) message to the customer. This SMS contains a single-use passkey, which the user then has to enter into the website to verify their identity.
Another common example of this type of Two-Factor Authentication is using a third-party authenticator app. Authenticator apps (such as Google Authenticator, Authy and Microsoft Authenticator) show a randomly generated and regularly refreshing code that can be used to verify the user’s identity instead of a code sent by SMS.
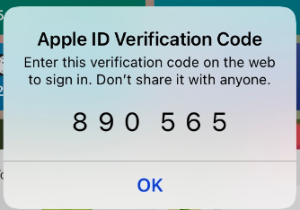
Apple in particular has an interesting take on this method. If you are trying to log in to your iCloud account from a new device (such as a computer),an authorisation key will automatically pop up on your existing device (such as your phone). Then, you enter the authorisation key from your phone onto your computer, verifying your identity to Apple. This is a convenient way that Apple has found to get around using an app dedicated to two factor authentication.
Whichever method your favourite website uses, please do use it. It really is the best line of defence for your account if you password is either hacked or stolen.
Other posts in our Cyber Security series
- Cybersecurity Basics
- Passwords
- Multi-Factor Authentication
- Emails and Phishing
- Browsers Physical Security

